Hello All.
Now with the disappearance of the TMG appliance that we all came to love and loath, there are only a few options out there for using as a reverse proxy for Lync. The few i think are
- Windows Server using IIS AAR for Proxy’ing
- KEMP Appliance / Virtual Machine
- Citrix Netscaler
For me option 1 isnt an option as i personally think using a Windows Server then bending it to be a RP isnt viable and one i wouldn’t suggest to my clients. Option 3 is only a option if you have a citrix netscaler going spare. Again i wouldn’t be rushing out to buy a Citrix Netscaler if i had other options.
That leaves the second option which is my default option for my clients who are looking to purchase a RP. You heard it hear first KEMP will become the default mantra of Reverse Proxy for Lync going forward.
In this blog post Im going to detail how you go about setting up a KEMP Applicance as a reverse Proxy. (Note: The setup is the same for the Kemp Range, but today within this guide i will be using a KEMP VLM100)
To start with you need information from your Lync environment around the external Web services. ie: Name etc. For me, my labs external web service is called LyncWebExt.northernlync.co.uk.
Also i will be requiring a public certificate for the KEMP appliance. There are many public authorities out there which can provide this. <At the time of writing GoDaddy are the most competitive in pricing for UCC Certificates) NOTE: If you have a wildcard certificate this can be used on the RP as well.
If you need information on how to create the certificate request follow the link > http://technet.microsoft.com/en-us/library/gg429704.aspx
***Please be sure your public cert has the following on it.
Subject Name / Common Name = <Your Lync External Web name> – LyncWebExt.northernlync.co.uk in my case
SAN Name = <Your Lync External Web name> – e.g. LyncWebExt.northernlync.co.uk in my case YES Put it in as a SAN as well!!!
SAN Name = <Your Lync ‘meet’ service name – e.g. meet.northernlync.co.uk
SAN Name = <Your Lync ‘dialin’ service name – e.g. dialin.northernlync.co.uk
SAN Name = lyncdiscover.<domain> – e.g. lyncdiscover.northernlync.co.uk
So with our information at hand and our certificate provisioned lets move onto the steps required to setup out Kemp.
ALSO: Typically the KEMP appliance for Lync Reverse Proxy, requires be located within your DMZ and NOT on your internal domain.!
Step 1
The appliance will come with a default IP of 192.168.101.1 . If your running a virtual KEMP appliance then you will see on the black linux dialog the IP address to which is the node. If you are running a hardware appliance plug an ethernet cable into eth0 on the front of the appliance and navigate to the above IP via a web browser
Once youve select the IP with the browser you will be prompted for a username and password. by default this is
Username = bal
password 1fourall
Step 2 – Base Line configuration
Now we are on the console of the appliance lets start making the base line changes around the IP’s, local users and passwords etc.
From the Home screen, select on the left hand side to ‘System Configuration’
Now select Interfaces, then eth0 and add the IP address to which you will administer the appliance in the future. <for my lab the IP address ive selected is 192.168.1.223/24 (/24 is the subnet range, so tweak this to suit your needs)
NOTE: once this is complete the appliance will reset itself onto that IP so be sure you can navigate to it.
Again from the Systems Configuration Menu we are now set give the appliance a name. To do this select local DNS Configuration, then hostname Configuration. Now add the hostname of your choice.
In my lab ive called in KEMPRP1
Next we will still using the Local DNS Configuration option – add out local DNS NameServer IP and also the DNS Search Domain name
Next we need to select the Route Management Option from the Menu and select default Gateway.
Jumping further down the left pane menu you need to select ‘system Administration’, then the user management option
At this point to can change the password for the bal account AND also create a new account with a new username. <I personally always create a username and password which only i know as a backup to loosing or someone changing the main account password>
So that is it for the step2 baseline config.
You can if you feel necessary add Logging Config etc. I wont go into enabling that as its simple and straight forward to setup.
Step 3 – Adding a Virtual Server
so jumping back up the menu tree to the top we are now going to create a virtual server. For understanding the virtual server is the DMZ IP address to which the appliance is listening on. e.g your public IP will come inbound to your Firewall, then the firewall should Nat this through to your DMZ on a natted IP address which will match the virtual server IP of your Kemp Appliance.!.
ok so the first step from selecting the virtual service menu is to select ‘Add New’
You will then be prompted for a Virtual Address, which needs to be the DMZ natted IP address! which for my lab is 192.168.1.228
The port you are attaching to this virtual address is 443 as all traffic bound for the Kemp RP will be routed through 443, Next add a service name as an identifier <LyncMobility>, then the last step the Protocol is TCP.
then click ‘Add this Virtual Service’
You will then automatically jump to the properties page for the Virtual Machine. This is where you do the main config and server creation.
by default you will have the name you gave the service, the service type of HTTP/HTTPS and activate/deactivate Server <Enabled by Default>
Now select to expand standard options.
Now remove the tick for > Transparency
Add put a tick in the > Use Address for Server Nat
Now select to expand the option for SSL Properties
then select the option for SSL Acceleration = Enabled ! NOTE: you will get a warning about no certificate being available for the appliance. just ok this.
Once in the SSL Properties select the reencrypt tick box
now add the public reverse proxy certificate we created earlier by selecting ‘add new’, Also don’t forget to add the intermediate certificate as well
— Ignore advanced Properties as nothing needs changing on this.
— If your appliance has the new ESP option, you can ignore this as well
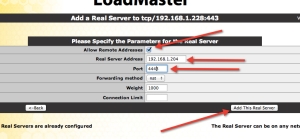
Now select the expand the Real Server Option, and select Add New
Now dependant on you default gateway you might be required to select an option in the miscellaneous option under network options to allow you to add a Real Server which is not in the default gateway IP range.
once you placed a tick in the option \> Enable non local Real Servers you will then get an option on the real server creation to bypass the check
Back on the adding of the Real Server, ive ticked the option to add a non local server, then added the IP address of my Lync Frontend, then we need to change the port to be 4443 for the internal routing, then we can select add
then select back, once you’ve had acknowledgement of the creation of the real server
last steps now, still on the real server option area select the checked port as 4443 and hit set checked port, then change the HTTP Method from HEAD to GET
Thats it. the set up is complete.
Jump back to Virtual Servers and select View. you will see your service as UP and working.
can from your Lync Mobile client log in with your user credentials.
ALSO you can see from the Home Screen graph traffic routing through
thanks for looking, and i hope it helps some of you out there.
**Special thank you to Bhargav at Kemp for providing my Kemp Licence.!









Another option is the reverse proxy from the only British load balancing vendor jetNEXUS
Thanks for this Gary..
folks look out for a full installation config guide running up against the JetNexus as a RP in the next few days
Regards
Iain Smith
Nice write up. What about internal wireless clients that are not on the domain.
this should be picked up via the lyncdiscoverinternal. setting within your Internal DNS.
Great article. I’m waiting on my 30 day demo license key from Kemp. Have you tested it with any iOS clients? Thanks. Rob.
Hello Rob
I can confirm the KEMP RP works with IOS, Windows Mobile, Android. All have been tested
Also to confirm you don’t get the full rich experience on the android devices.
Regards
Iain Smith
If I have 2 Kemps in HA and I have 2 Edge Servers in a Pool, how should I configure the Pool in Lync 2013? I selected that I am using NAT and entered both edge server’s; internal, external, and NAT External IP but since I am running through the Kemp should I only need one and then have the Kemp forward to the pool? Would I set up 2 Virtual Servers on the Kemp?
Also I was using one name and IP for all three(A/V, DialIn, etc).
I have not tested yet but wondering as I set this up and before I published the topology.
Good Morning Clay
ok for my understanding, i read that you have the following
you have a pool (meaning you have Lync 2013 Frontend Enterprise Edition)
you have two kemps in HA configuration
you have two edge severs pooled
From the outsite (external) to the Kemp.
Your edge servers will be serviced from single external IP addresses for your ‘sip, wc, av’ FQDN’s. On user/client request this will then/should hit your perimeter firewall which then should allow and NAT the IP to the virtual IP of the KEMP.
You kemp will then, on rules will allow the traffic through to the Lync 2013 front ends.
**another question is?
why are you putting a kemp in against the edge servers? this is not a requirement as such and maybe overkill for what you need?
***
also another option if you want to go down the KEMP route, would be to add the KEMP’s into your internal domain and also utilise them for HTTP traffic balancing as part of your internal frontend service.
Thanks
Iain Smith
I am receiving a: Bad HTTP status received. Then the Kemp reports it is taking it out of service due to failed Real Servers. Have the Kemp setup in a dual arm configuration but I tried putting the default gateway of the service to be the firewall. I have a firewall rule to allow 443 and 4443 traffic through the DMZ to inside. Not sure what to check.
I am receiving the same Bad HTTP status message in the Kemp LB logs. The status for the virtual service is down and will not come up.
Removing RS 192.168.1.22:4443 from VS 192.168.1.202:443(LyncMobility) – Bad HTTP status received
VS 192.168.1.202:443(LyncMobility) Taken out of service due to failed Real Servers
Has anyone found what is causing the error?
Hello Mark
I’ve found this issue actually as well. Oven ever got to the bottom of it, but changing the 4443 to 5061 works and solves this issue.
It’s like the 4443 isn’t allowed through the firewall of the frontend server
Another thing I found that will make the connection come up and still leave the port as 4443, is if you specify a valid URL path. I set mine to /ucwa (this is valid path in the Lync Server External Web Site. Not sure what impacts this would have on the reverse proxy behavior?